Sophos UTM has arguably been one of the most impactful and disruptive firewall products on the market over the last few years. The UTM 9 platform, with compelling updates and the passionate support of our partner community and customer base, has helped Sophos UTM achieve unprecedented success in the market.
We’re as committed as ever to continuing this success with our first update of the year: UTM Elevated 9.4.
Most modern firewalls today support IKEv2, but some (such as the Sophos XG firewall) do not. Check with your vendor to validate support. If the firewall or VPN device supports IKEv2 for remote access connections, the native Windows VPN provider can be used to establish an Always On VPN connection.
Why “Elevated”? Well, by including the option of adding Sophos Sandstorm to Sophos UTM, we’ve raised protection levels to all-new heights. Sophos Sandstorm lets you add enterprise-class sandboxing to your small and mid-size business networks. It directly addresses today’s ever-more evasive threats and raises the bar for delivering effective, affordable advanced threat protection.
In addition to providing access to the new Sophos Sandstorm, the UTM 9.4 release also adds some of your top-requested features including new WAF and VPN features as well as support for a number of new hardware options further extending our top-performing hardware line up. Read on to view the details.
- Because IKEv1 is not compatible with IKEv2, maybe you have a choice which protocol you will use. Sophos UTM Community Moderator Sophos Certified.
- Sophos UTM and AP15: fixing “llread: dead socket: Resource temporarily unavailable” Sophos’ access points are very sensitive with PoE enabled cable connections. If your access point gets disconnected, disable PoE for the given Ethernet port. As a long time reader of my blog, you might know Read more.
- Sophos doesn't seem to have an easy or automated way to update the ever changing list of web addresses to whitelist for full Office 365 support. I've seen the KB for the XG firewall but since as far as I know there is no way to import that list into UTM, is there any easy way to automate this or at least make it easy to enter?
Extending zero-day protection
Today’s hackers are employing more targeted attacks with highly evasive never before seen malware designed to breach security systems to gain access to a company’s resources, credentials and data. So while conventional anti-malware is still a critical first line of defense, it’s no longer enough in combating modern attacks.
Most next-generation sandboxing solutions designed to identify unknown malware are too complex and expensive for most businesses like yours to even consider. That’s why we’ve developed Sophos Sandstorm, a new subscription option that gives you an advanced malware defense solution that’s effective and affordable. Sandstorm is a cloud-based sandbox solution that provides targeted attack protection, visibility and analysis that rises above the competition.
It’s simple:
- Easy to try – sign up through MyUTM and benefit from instant protection
- Easy to deploy – simply activate the policy
- Easy to manage – through your usual UTM workflow
It’s effective:
- Blocks evasive threats – detects threats designed to evade sandboxes that other solutions miss
- Policy control – simple, efficient policy control
- Visible protection – granular, incident-based reports
It’s cloud-based:
- Rapid deployment – instant protection with no hardware to deploy or appliance upgrade needed
- Minimal impact on performance – all processing done in the cloud
- Collective intelligence – analysis of threats detected across the broad Sophos customer base
And perhaps most importantly, it’s affordable. Sophos Sandstorm will be available in UTM 9.4 as a new Protection Subscription, at a great value price-point compared to competing enterprise solutions in this category. It’s enterprise-grade protection without the enterprise-grade price tag or enterprise-grade complexity.
Expanding the hardware lineup
UTM Elevated 9.4 adds support for a number of new hardware options, further extending our top-performing hardware line up.
SG 85(w) brings new New SG Series Appliances to the low-end of the line. The SG 85 is available in both an integrated wireless (w) model and without wireless. It is ideal for extremely price-sensitive deployments like retail or SOHO. Expected availability of the SG 85(w) is March 2016.
4x10G SFP+ Flexi-Port Module for the 1U SG Series models brings a whole new level of flexible connectivity and performance with four port support for a variety of optical or electrical transceivers. Expected availability is March 2016.
RED 15w adds integrated wireless to the new RED 15 with a single radio supporting 802.11n 2×2:2 MIMO. Expected availability is March 2016 with similar (aggressive) pricing to the new XG 85w.

AP 15c packages the popular, new and affordable entry-level access point into a ceiling smoke-detector type chassis. It offers the same great performance and value as the AP 15 desktop model with a single radio with 300Mbps of 802.11n throughput – but now with a choice of band (either 2.4GHz or 5GHz). Expected availability is March 2016.
Enhancing the firmware features
UTM Elevated 9.4 also delivers some of your top-requested features.
WAF Persistent Session Cookies improve the user experience when interacting with business applications protected by the Sophos UTM, reducing repeated sign-in prompts.
STAS (Sophos Transparent Authentication Suite) provides reliable transparent SSO authentication for network users, without requiring a client on the endpoint. STAS employs an agent on the Microsoft Active Directory Server that monitors and stores authentication activity and exchanges authentication information with the UTM, making user-based policy rules and enforcement easy.
IPv6 SSL VPN Support adds much requested support for IPv6 VPN connectivity with the UTM.
Looking beyond
While UTM Elevated 9.4 is a substantial release, it’s one more in what has been, and will continue to be, a great series of updates to this award-winning product. We have even more great plans for this product with UTM 9.5 and 9.6 releases already in the early planning stages, promising to bring you even more value, simplicity and security.
Image of flying airplane courtesy of Barn Images.
This article explains how to configure IPSec VPN Site to Site between Sophos XG firewall and Pfsense firewall devices
This aritcle configured according to the following diagram:
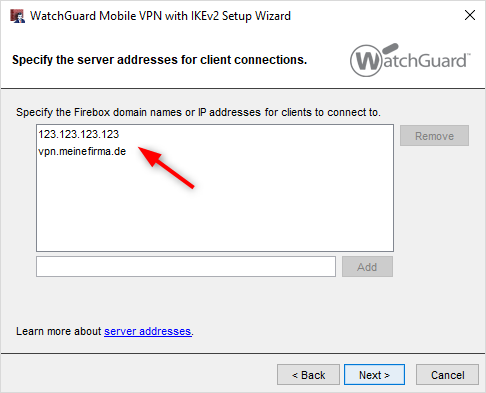

How to configure
Configure on Sophos XG
Step 1: Create Local and Remote network area for XG device
- Log in to Sophos XG by Admin account
- Hosts and Services -> IP Host -> Click Add
- Create Local Network
- Enter name
- Choose IPv4
- Choose Network
- In IP address -> Import Internal network
-> Click Save
- Create Remote Network
- Enter name
- Choose IPv4
- Choose Network
- In IP address -> Import Remote network
Ikev2 Sophos Utm Software
-> Click Save
Step 2: Create IPSec connection on Sophos XG
- VPN -> IPSec connections -> Click Wizard
- Enter name
- Click Start
- Choose Site To Site
- Choose IKEv2
- Click >
Sophos Utm Ikev2
- Choose Preshared key
- Enter Preshared key (using for both site)
- Click >
- Choose WAN port of Sophos XG
- Choose Local Network which is created before
- Click >
- Enter IP WAN of Pfsense
- Choose Remote Network which is created before
- Click >
- Choose Disabled
- Click >
- Click Finish
- Click Active
Configure on Pfsense firewall
Step 3: Create IPSec connection on Pfsense (P1)
- Log in to Pfsense firewall by Admin account
- VPN -> IPSec -> Click Add P1
- In Key Exchange version: Choose IKEv2 (same with Sophos)
- In Internet Protocol: Choose IPv4
- In Interface: Choose WAN
- In Remote Gateway: Enter IP WAN of Sophos
- In Authentication Method: Choose Mutual PSK
- In Pre-Shared Key: Enter Preshared Key which the same with Sophos
Ikev2 Sophos Utm 9.7
- In Encryption Algorithm: Choose AES -> 256 bits -> SHA256 -> 14 (2048 bit)
- In Lifetime (Seconds): Enter 3600
-> Click Save
Step 4: Create IPSec connection (P2)
- In Local Network: Choose Lan subnet
- In Remote Network: Enter Local network of Sophos
- In Protocol: Choose ESP
- In Encryption Algorithms: Choose AES -> 256 bits (same with Sophos)
- In Hash Algorithms: Choose SHA256
-> Click Save
Step 5: Create Firewall rule in Sophos to allow VPN and LAN network connect together
Step 6: Click Connection to finish
Configure create Firewall rule for Pfsense to finish
** If you have difficulty configure Sophos products in VietNam, please contact us:

Hotline: 02862711677
Email: info@thegioifirewall.com
YOU MAY ALSO INTEREST
